Üdvözlünk a(z) Orpheus adatlapján!

Profil adatok
| Elérhetőség | Link az oldalhoz |
| Szint | 8 |
| Típus | Zene |
| Felhasználók | 2647 |
| Torrentek | 688608 |
| Regisztráció | Meghívós |
| Arány | Közepes |
| Nyelv | angol |
| Az oldal alakult |
További bemutatók
Egyéb
| Az oldal jelenleg: | Online |
| Elérési állapot: | 0 (magyarázat) |
| Kapcsolat: | |
| Kapcsolattartó: | |
| IRC: | |
| Hasonló oldalak: | |
| Adatlapot beküldte: |
Anonymus 2018-11-04 |
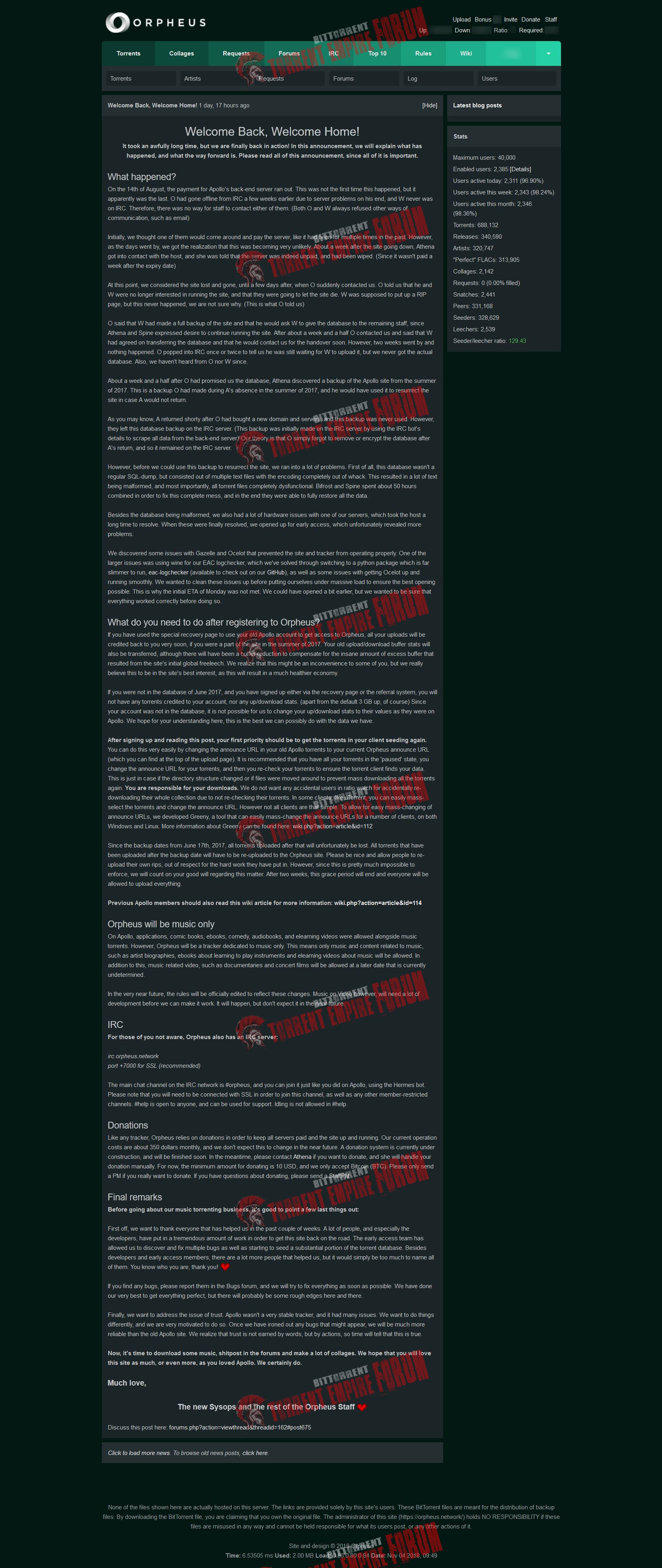
Legfrissebb hírek
AoTM February Round 1 Winner & Round 2 Voting Open - 16.02.25
AoTM February Round 1 has closed and we have a winner!
AoTM February Round 1 Winner - Here And Now - Give And Take
Congratulations to keasyman for their winning pick. 20,000 Bonus Points have been added to your account.
This album will be Freeleech for two weeks (FLAC only)
Voting is open and all nominations are Neutral Leech.
AoTM March Nominations are open.
A most unfortunate set of circumstances - 04.02.25
People who were online yesterday received the surprise of seeing various sensitive site configuration values in place of the expected website. How that happened was a perfect storm of circumstances, that have been addressed to avoid it from happening in the future, and all the exposed values have been rotated. No user data was at risk at any time.
Here is the post mortem of the incident.
To understand it all, we have to go back a number of years and begin with the original what.cd Gazelle codebase. The architecture for setting up configuration variables back then was rather cumbersome and awkward to maintain. As I recall, it was a plain text file of key/value pairs and it was quite easy to make errors when making changes. And it probably meant that a lot of developers who worked on Gazelle at the time found it easier to just hard-wire the number they needed, where they needed it, rather than make them easy to reconfigure.
One of the changes we made years ago was to change the configuration data to a PHP file, so that the interpreter would catch errors as soon as it was loaded. If there was an error, the site would show a white screen of death. After this, it became easy to pull out a lot of magic numbers from the code and turn into (documented!) configuration variables.
The next problem encountered was that it was cumbersome to keep separate the default values required to bring up a site, and the values a specific site needs (like database passwords). Another change was made to address this, in that the default configuration file would be "good enough" for most needs, here or elsewhere, and only a small number of variables would need to be overridden to tailor behavior for any given site.
Fast forward to a third issue we ran into, where a misconfiguration on the front end proxy would dump the PHP code of the main page of the site. So that part of the site was also revamped to show only require gazelle.php; on a page if something went wrong.
And then we get to a fourth problem. In revamping that code, I ran into what I had remembered as being a termed a Gate Problem, which, in the literature, goes by the name of a Chesterston Fence.
G. K. Chesterton was a philosopher and in regards to the economics of political reform, formulated the following parable:
There exists in such a case a certain institution or law; let us say, for the sake of simplicity, a fence or gate erected across a road. The more modern type of reformer goes gaily up to it and says, “I don’t see the use of this; let us clear it away.” To which the more intelligent type of reformer will do well to answer: “If you don’t see the use of it, I certainly won’t let you clear it away. Go away and think. Then, when you can come back and tell me that you do see the use of it, I may allow you to destroy it.”In relation to Gazelle, there was a pair of statements at the beginning and end of a large section of code that had the effect of saying "if anything wants to output stuff to the page in this section... just throw it away". And when I refactored the code, I did not think hard enough about its use and how anything could like that could happen, and removed the two statements.
And then there is a final situation that was needed to align with the rest, the blame of which belongs to PHP itself. PHP is a funny language, in that, by default, it assumes somewhat paradoxically that a file you want it to execute does not contain any PHP code. It assumes the file is text, perhaps HTML, and must be sent to the browser. To instruct PHP that, yes, there is actually PHP code to interpret, the source code file must contain "<?php" From that point on, the PHP interpreter will interpret the rest of the file as php code. No other language behaves this way.
And finally we get to yesterday. I was working on a merge request in the CI which will change the names of a couple of configuration variables in the override file. As I looked them up, I noticed an old key belonging to retired code that no longer serves any purpose. So I deleted it, as there is no point keeping obsolete code present.
And this is where we get to the crux of the matter. I was working in the CI and not looking at the site, and for reasons I will never fathom, I managed to move to the top of the file and repeat the operation, deleting the first line. After that, first line no longer had the opening "<?php" and the interpreter faithfully dumped it to the browser, which I missed completely.
And as a result, a series of sensitive configurations were posted at the top of the page. Sensitive in that yes, if one had access to the server, you could log into the database and exfiltrate any amount of data. But there was never any risk of that. The backend server is so heavily firewalled off that even if you knew the server address, scanning it would reveal no open services, no means of purchase to get inside. There were also some internal network addresses that reveal little, and some other minor things like exact ids of wiki pages. Since then, all of the sensitive values have been reset to new values. At no time was any personal data like email addresses or announce keys ever in danger of being exposed. And yes, the bit of code that loads the configuration file now has the safeguard code back in place to prevent it from ever again being spewed out by accident.
The biggest visible consequence of this (apart from having to log in anew) is that we have pushed forward with the planned changes to RSS feeds. Now you will definitely need to update your feed addresses to get new data, as the internal signature key value was changed and the old URLs no longer work.
And so all of that is why we took the site down: to change what needed to be changed, and update what needed to be updated. My humble apologies. This, at least, will not happen again.
AoTM January Round 2 Winner & February Round 1 Voting Open - 01.02.25
AoTM January Round 2 has closed and we have a winner!
AoTM January Round 2 Winner - Lalo Schifrin - Black Widow
Congratulations to phukengruven for their winning pick. 20,000 Bonus Points have been added to your account.
This album will be Freeleech for two weeks (FLAC only)
Voting is open and all nominations are Neutral Leech.
AoTM March Nominations are open.
Roll on 2025 - 01.01.25
Happy New Year!
May your musical discoveries this year be numerous and enjoyable. Here is the latest news.

Join our FLS and IN teams
If you are enjoying Orpheus and would like to help out a bit more, we need to boost our First Line support, and especially our interviewers. Both teams are crucial in helping the site to continue to grow and the Interview team is critically short-staffed. If you can set aside a hour or so with regularity each week, it would be gratefully received.
Apply within
Push Notifications
Thanks to the heroic efforts of s****, the push notification infrastructure (the thing that sends you alerts to your phone) has been rebuilt pretty much from the ground up. Find out more about it in Wiki › Push notifications.
Some notification types have not yet been wired up to the new machinery yet, but the big ones are there. Let us know if you run into any issues.
If you dislike the pop-up notifications box, you can also set all notifications to display at the top of the screen.
Check it all out in your profile settings!
Request searches
With the combined efforts of c**** and m***, various bugs in requests search have been fixed, the user interface has been made smarter, and for the first time ever, the "Only specified" toggle works.
When checked, this toggle excludes requests that do not explicitly specify the desired property. For instance, choosing "CD" will exclude all other media, including the "Any" catch-all. Choosing "CD", "WEB" will return only the requests that explicitly request "CD" or "WEB" (hence a request asking for both "CD" and "WEB") will be returned.
When the toggle is left unchecked, all the requests specifying "Any" will be returned as well.
Minor updates
Add img proxy url to torrent endpoints has been implemented. The arguments as stated are persuasive and the change was literally two lines of code (one of which is a unit test).
Coming up
There are two changes coming up, to which we would like to draw your attention, both concerning security.
Announce URLs
The first change concerns the way you bittorrent client connects to the tracker. Currently, the tracker allows both plaintext (http) and encrypted (https) connections. On July 1st (2025-07-01), support for plaintext connections will be turned off. Any torrent that uses and http announce will error out at that point. There will be further announcements before this date to assist with the migration.
RSS Feeds
The second change will impact everyone using RSS feeds.
Why?
We recently upgraded the site, and migrated to PHP 8.4. One of the features that has been deprecated in this new version are MD5 and SHA1 digests (which are used in various places to authenticate secrets). We can change everything transparently so that people benefit from the greater security that SHA256 offers (which is what we will be changing to).
But not feeds. This is the only place that cannot be changed transparently. We will be reaching out to people who are using the current version to tell them to upgrade.
RSS links look like this:
feeds.php?feed=torrents_all&passkey=<passkey>&auth=<md5-signature> where the auth parameter is 32 hexadecimal characters (0-9 and a-f).
In the new version, the auth parameter is now comprised of alphanumerics and is 44 characters long. As an additional security improvement, auth is now unique per feed, rather than being shared.
The old feeds will continue to be honored until they are retired in six months time (July 1, the same date as above). Users must upgrade before then.
An important reminder, RSS links contain your torrent passkey! A passkey is as valuable as a password. Do not paste them anywhere public, especially in IRC or the forums if you require help.
A gift for the New Year
As a gesture of goodwill regarding the incident that affected many of you last year, we are forgiving 25 gigabytes of download data. That is, if your download statistic is greater than 25GiB, it will be adjusted downwards by that much. If you have less than 25GiB down, it will be become 0 (and your ratio becomes ∞ a.k.a infinity).
Enjoy!
With 
Orpheus Staff
AoTM: February Round 1 Winner & Round 2 Voting Open - 12.03.22
AoTM: February Round 1 Winner & Round 2 Voting Open
AoTM February Round 1 Voting has closed and we have a winner!
AoTM February Round 1 Winner: John Lennon / Plastic Ono Band
Congratulations to a*** for their winning pick. 20,000 Bonus Points have been added to your account.
This album will be Freeleech until the next round (FLAC only)
Voting is open for ten days and all nominations are Neutral Leech.
AoTM March Nominations are open.
By CF dealerKépek az oldalról:
Megtekintve:1654 alkalommal

